Government Cyber Security Policy Handbook
This Government Cyber Security Policy Handbook supports departments to build capabilities which meet the requirements of the Cyber Assessment Framework (CAF), through drawing on government policy, technical guidance and available toolsets and structuring these in the language of the CAF.
Introduction
The Government Functional Standard GovS 007: Security sets expectations for protecting:
- The government’s assets (people, property and information).
- Visitors to government property, and third party suppliers whilst engaged on government business.
- Citizen data.
Government organisations are required to have the mechanisms in place to identify and manage known risks in order to maintain a proportionate and effective level of cyber security across all government organisations. As part of this, organisations that handle government data and information are required to assess their cyber resilience against the appropriate government profile under the NCSC’s Cyber Assessment Framework (CAF). This security standard consists of outcomes, allowing organisations flexibility in how the standards are implemented, dependent on their local context.
This Government Cyber Security Policy Handbook supports departments to build capabilities which meet the requirements of the Cyber Assessment Framework (CAF), through drawing on government policy, technical guidance and available toolsets and structuring these in the language of the CAF.
Structure
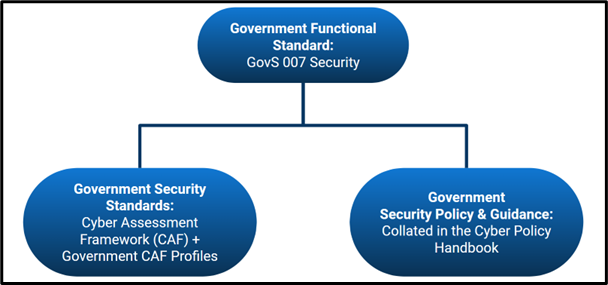
The above image depicts how the Government Functional Standard for Security GovS 007 sets high-level security requirements for all government organisations. It establishes the foundation and aims of the subject-specific standards which sit underneath. For cyber security, this standard is the Cyber Assessment Framework, which sets outcomes based requirements for government organisations. This is accompanied by security policy and guidance, which reinforces the standard and supports government organisations meeting its requirements.
How to use this suite
The contents of this suite should not be considered the only means of achieving Indicators of Good Practice (IGPs) under the CAF. Separate guidance will be provided as a handrail for departments to navigate the GovAssure end to end process and give examples of demonstrated outcomes. Departments will use security controls appropriate to their environment and some will exceed the recommended baseline. This resource is aimed at providing that baseline.
As part of this handbook both policy and guidance may be outlined under each principle.
Policy
Policy is understood as the mandatory requirements that are placed on each government organisation which should be complied with as closely as possible, either as broader security principles or where particular measures closely support the Government Cyber Security Strategy (GCSS) ‘Defend as One’ pillar. Where relevant we have recorded the ministerial or official communication stipulating the adoption of this policy.
Note: Policy requirements stated here will include those that sit outside of the CAF, but are relevant to the area in which they are included.
Guidance
Guidance is advisory only and should support teams in meeting their strategic objectives. This may include specific tooling or measures where considered relevant for meeting core CAF outcomes, or which contribute to the GCSS ‘Defend as One’ pillar.
Additional guidance will be provided where the GovAssure Enhanced Profile requires a more advanced level of capability to achieve its relevant IGP.
GovAssure Baseline and Enhanced Profiles
The threats faced by a department or organisation’s core government functions and services have shaped the development of CAF profiles for government which will be applied as part of GovAssure. To enable an effective approach to dealing with the different threats there are two CAF Profiles for government.
Baseline Profile
The Baseline Profile constitutes the minimum baseline standard for all departmental or organisational cyber security controls. The profile looks to mitigate risks presented by average to lower attacker capability and considers threats from primarily non-targeted attacks.
All government organisations are to be assessed against the Baseline profile at minimum.
The Baseline Profile was developed by modelling the most likely impactful attacks against government and determining which IGPs against the CAF outcomes would mitigate those attacks.
Enhanced Profile
The Enhanced Profile layers additional CAF IGPs for systems where risk owners define a more cautious risk appetite against cyber attacks, including against more persistent and capable actors, and may have lower tolerance for risk.
These IGPs contain additional security controls which are more advanced and require more mature security capability to implement.
A system may be identified as requiring the Enhanced Profile through determining its threat profile, which will include assessing threat vectors, whether the system supports Critical National Infrastructure (CNI), system criticality and criticality of the data which it stores or processes.
Framework Revision and Feedback
The Government Cyber Security Policy Handbook will be kept under regular, formal review to ensure that it remains accurate and up to date as a resource. We also invite departments to email gsgcyber[at]cabinetoffice.gov.uk to propose any updates and make suggestions on areas where additional policy and guidance is required. These will be reviewed accordingly.
Overarching Government Policy and Guidance
There are some pieces of guidance which apply across CAF principles and should be referred to throughout by organisations when approaching GovAssure:
- Securing your information provides government guidance on considering information security in the context of OFFICIAL government data. It provides information on how to understand information risk, conduct an effective risk assessment and utilise the assessment findings to prioritise risks for mitigation through a variety of controls.
- The Technology Code of Practice is a set of criteria to help government design, build and buy technology. Within this framework, Section 6: Make things secure sets out requirements for considering system risk when building a system, embedding proportionate security controls and assuring that risks have been appropriately mitigated. Additionally, Section 9: Make better use of data stipulates steps for the effective management and sharing of data throughout its lifecycle through to archive or deletion.
- The Central Digital and Data Office (CDDO) has developed Secure by Design principles for government. These principles will enable organisations and programme delivery teams to adopt a common approach to securing digital services: they embed appropriate, proportionate cyber security measures in digital services from the start. They also ensure that risks are continually identified and managed, and security posture is assured throughout the digital lifecycle.
Each principle section within the Government Cyber Security Security Policy Handbook also contains a ‘Further information’ section, which points to the NCSC CAF Webpage and their recommended guidance for each principle.
Principles
- Principle: A1 Governance
- Principle: A2 Risk Management
- Principle: A3 Asset Management
- Principle: A4 Supply Chain
- Principle: B1 Service Protection Policies and Processes
- Principle: B2 Identity and Access Control
- Principle: B3 Data Security
- Principle: B4 System Security
- Principle: B5 Resilient Networks and Systems
- Principle: B6 Staff Awareness and Training
- Principle: C1 Security Monitoring
- Principle: C2 Proactive Security Event Discovery
- Principle: D1 Response and Recovery Planning
- Principle: D2 Lessons Learned
Author: GSG Cyber Security Policy Team, Government Security Group (GSG), Cabinet Office
Contact: gsgcyber@cabinetoffice.gov.uk
Last updated: 06 April 2023